The RF in RFID: physical layer operation of passive UHF tags and readers
Daniel M. Dobkin
(revised August 2021)
6. RFID Protocols
A communications protocol is a way of organizing the conversation between devices -- in the case of RFID, between tags and a reader -- to ensure that information actually gets transferred. A protocol defines:
an air interface: what sort of modulation of the reader signal is used to define a binary one? what's a zero? what kind of signal does the tag send? how fast does everything go? is information sent in discrete packets, and if so how are they formed?
medium access control: who gets to talk when? how are collisions between contending users (tags in this context) resolved?
data definitions: what sort of data is associated with a tag? what does it mean?
Passive RFID tags face some special problems not encountered in most other digital radio systems. Tags are cheap and dumb, so only changes in amplitude of the reader signal can be used; advanced modulations like phase-shift keying or quadrature-amplitude-modulation (QAM) are not available. Further, turning off the power from the reader reduces the power available to the tag, so the modulations of choice for the reader are those in which power is on most of the time; such modulations are wasteful users of spectrum, leading to realtively wide channels or low data rates. The tag reflection can be modulated in phase or amplitude, but the small tag reflection is combined with large reflections from the antenna and ambient, so that the resulting signal at the reader may change amplitude when the tag reflection changes phase, and so on. One can only hope to detect changes in state of the tag antenna, but not the type of change. The reader can count edges from the tag but not the absolute or differential phase or amplitude. Tag and reader symbols must be chosen with these constraints in mind.
There are numerous protocols using different approaches to each of these issues, and all of them work -- but the reader and tag need to use the same one! In this discussion we'll briefly examine the UHF tag protocol that has been promulgated by EPCglobal (now part of GS1) for supply-chain tracking using passive RFID tags. The EPCglobal protocols assume the tag carries a unique identifier, the electronic product code (EPC). EPC's can be either 64 or 96 bits long (longer ID's are available for future use), and are partitioned into a header describing the EPC structure, some information about the 'manager' (typically a company owning some ID space), and other information about the type of object marked and the serial number.
At the time of this writing (2021), the old Class 0 and Class 1 Generation 1 protocols, as well as most other older proprietary and standardized UHF passive protocols, have been substantially displaced by Class 1 Generation 2 (ISO 18000-6C), so the reader short of time may wish to skip their descriptions. However, it is interesting and educational to see alternative methods of solving common problems, so I recommend perusing the older standards if you have the stamina; brief descriptions thereof are found here.
EPCglobal Class 1 Generation 2 (ISO 18000-6C = 18000-63)
First-generation standards had some significant disadvantages. It was awkward to address a specific tag, particularly if you have erased the EPC in the course of assigning a new code to the tag. The use of a 16-bit CRC as the only validation of a tag ID means that on average one in 64,000 reads of random noise would produce an accidentally valid tag read -- a phantom or ghost tag. Class 0 tags had problems with large numbers of collocated readers due to the large frequency offset between the tag signal and the reader signal, and had no standard for field writeable tags. Class 1 singulation was relatively slow when a large number of tags are present. Both protocols have problems with late arrivals: tags that enter the read zone when a tag inventory has already started. Finally, class 0 and class 1 were mutually incompatible and approximately equivalent in applications and performance: if the goal is to achieve one global standard, two is one too many.
Realizing these problems, the EPCglobal Hardware Action Group in early 2004 started work on a second-generation standard that would fix the problems in the first-generation standards and provide sufficient performance at sufficiently low cost to become the universal protocol for RFID in supply chain applications. The Class 1 Generation 2 standard was ratified in early 2005, and subsequently ratified by the International Organization for Standardization (ISO) as ISO 18000-6C; the standard has migrated to the new number 18000-63, but is still often referred to as "6C" by practitioners in the field. In order to obtain the aforementioned improvements in performance, the Gen 2 committee started anew in many respects; the Gen 2 standard is completely incompatible with first-generation class 0 and class 1 readers and tags.
The reader symbols are distinct from those older standards. A binary '0' is a short high level pulse followed by low pulse of equal length; a binary '1' is a longer high pulse followed by the same low pulse width. This symbol set provides a high average RF power delivered to the tag. The length of a binary '0' is defined as Tari, and is used as a reference for several other times in the standard. The data rate can vary from 27 to 128 Kbps (Tari from 25 to 6.5 microseconds); the most significant bit of the most significant word is always sent first.
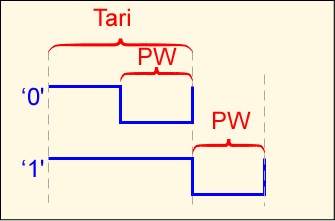
Communication between the tag and reader is packetized. The reader sends a query or command and then transmits continuous (CW) power while a tag hopefully responds.
Two distinct sets of tag symbols are used. The basic approach is FM0: a binary '0' has a transition in the middle of a symbol, whereas a binary '1' does not. However, a second option is provided, Miller-modulated subcarrier (MMS). The FM0 signal is multiplied by a square wave with either 2, 4, or 8 periods for each FM0 symbol. It is important to note that, although in the figure below we show the FM0 symbol time as constant so you can see how the transmitted signal is related to the FM0 signal, in fact it is the time between transitions, or equivalently the link frequency, that is held constant. As a consequence, the data rate for a fixed link frequency is reduced by the MMS multiplier. If we set a link frequency of 100 KHz, FM0 provides a data rate of 100 Kbps, but MMS with a multiplier of M=4 only provides 25 Kbps.
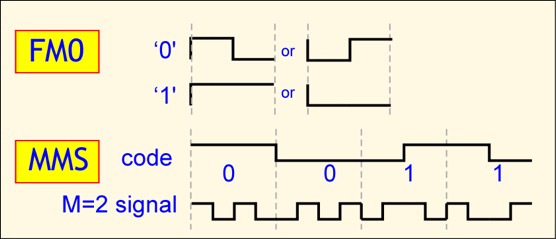
It seems contradictory to intentionally reduce the data rate, but MMS offers some advantages over FM0. In spectral terms, the energy in an MMS signal is concentrated away from the carrier (roughly by the link frequency), making it easier to detect in the presence of phase noise and possible interference from other readers. In the time domain, interpretation of an FM0 symbol depends on a single edge, whereas an MMS symbol provides a number of edges to locate, reducing the likelihood of a bit error.
Inventory operations are based on slotted Aloha collision resolution. The reader issues a QUERY command, and each tag effectively rolls a many-sided die, where the number of sides is set by the reader. A tag that rolls a 0 replies immediately; all tags that roll other numbers record those numbers in a counter and say nothing. The reader, after either receiving a reply or no response, can issue a QUERY REP command, causing all the tags to decrement their counters by 1; any tag reaching a counter value of 0 responds. If the number of sides is chosen properly, one and only one tag will respond to most of the QUERY REP commands.
A tag replies by sending a 16-bit random number RN16. If the reader hears the random number it echoes that number as an acknowledgement, causing the tag to send its electronic product code and error check, along with some protocol control bits (PC). The PC bits provide the length of the EPC stored in the tag, as well as some information pertaining to the numbering system and optionally the type of object to which the tag is attached (the application family identifier (AFI)). The reader can then send commands specific to that tag, or continue to inventory other tags.
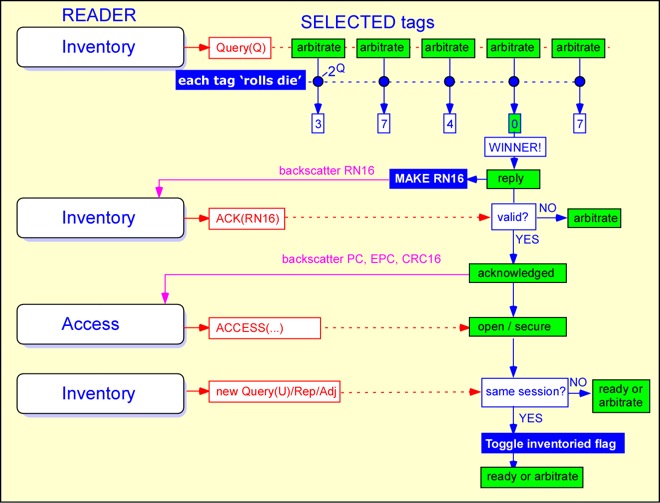
The use of a random number as a handle is an important feature of the Gen 2 protocol. This allows the reader to define a unique session with a particular tag even if that tag has not been identified, or does not have a unique EPC (e.g. if it has just been received from the factory with its EPC initialized to all 0's). A Gen 2 reader can count tags in the field even if all the tags have the same EPC. It can write to a single tag even if that tag has not yet been given a unique identifier. Furthermore, the sequence of exchanging a valid RN16 followed by transmission of the EPC makes it less likely that the reader will see a ghost or phantom tag where none is present.
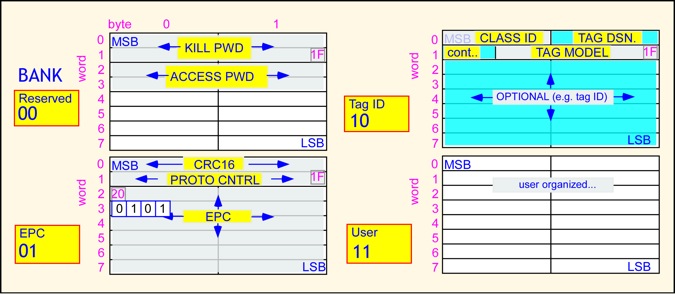
The Gen 2 standard specifies the tag's memory organization. Memory is organized in 4 banks, organized into 32-bit words. Bank 00 is reserved for passwords for the lock and kill functions. Block 1 contains the protocol control bits, the error check, and the unique identifier, normally the EPC. Block 2 contains information about the tag, possibly including a unique tag identifier distinct from the EPC (that is, a number identifying the tag itself and not the object to which it is attached). Block 3 is user memory and may be organized in any fashion. A SELECT command, that works somewhat like the class 1 filter command, is available to choose tags which are to participate in a given inventory session. Recent updates to the standard expand upon the protocol control word to support additional capabilities, such as simple sensor data and battery-assisted tag operation.
A more detailed discussion is also presented in my RFID book, in which you'll get acquainted with the International Organization for Contention (IOC), and the STAR (Slothful Tag And Reader) protocol working group (mis)managed by the illustrious Toulouse Track.
The ISO 18000 suite describes a series of passive tag standards. 18000-6A and 18000-6B = 18000-61,62 are distinct UHF tag protocols. A few aspects of the standards are common, but the modulations, symbol sets, and command sets and mostly incompatible. At the time of this writing (2021), 18000-6C has become the most common worldwide standard for UHF passive tags in supply chain applications. ISO's 18000-related working groups have continued to develop enhancements.
The EPCglobal standards are specifically designed for supply chain applications. There are a number of other RFID protocols applicable to UHF operation, as well as numerous standards for LF and HF ("near-field") tags and readers.
